It wasn’t a Wi-Fi router, although it appeared like one. Inside its modern, rectangular shell, lots of of calls had been being routed from Cambodia to unsuspecting victims throughout India. In this unremarkable two-storey home in south Hyderabad, a worldwide cybercrime syndicate had discovered an unlikely headquarters.
For weeks, the kitchen doubled as a command submit. As the household stirred curries and packed lunchboxes beneath, 28-year-old Hidayatullah climbed as much as the shelf on cue from his abroad handler, swapping SIM playing cards, checking the facility connection and resetting the gadget.
To his neighbours, he appeared like every other younger man; typically residence, shifting round in monitor pants and a unfastened T-shirt, hardly ever stepping out besides to gather meals deliveries. To his household, he was merely between jobs. They had no cause to suspect that their kitchen had was a nerve centre of a multi-crore prison enterprise.
That phantasm shattered when the police got here knocking on September 11.
Investigators say Hidayatullah had reassured his ageing dad and mom, his brother, sister-in-law and younger nephew that he had “lastly discovered work the place he may mint a great deal of cash”. He warned them to not query him about his work or the gadget, even threatening to finish his life in the event that they did. For months, the household continued with their routine, unaware that their residence was a hub connecting scammers in Cambodia to victims throughout Telangana and past.
Hidayatullah’s path to crime wasn’t deliberate; it was determined. Once a automotive vendor, he had watched his life unravel in fast succession: first shedding cash to dependancy, then to a fraudulent funding scheme that worn out over ₹16 lakh. Cornered and hopeless, he turned to the identical buddy who had lured him into the funding fraud. This time, the buddy launched him to a girl named Venisa, primarily based in Cambodia, who promised a technique to get well his losses.
Her directions had been easy, however sinister: set up a SIM field at residence, join it to broadband and feed it with SIM playing cards. Each name it dealt with could be a part of a classy community that blurred worldwide routes, spoofed caller IDs and allowed fraudsters to pose as authorities officers. Hidayatullah could be paid for “visitors”, every blink of the gadget translating into revenue.
But retaining the machine alive required lots of of SIM playing cards, and that’s the place his community got here in. Apart from him, police arrested two others, each authorised point-of-sale (POS) brokers for Vodafone and BSNL. One of them, simply 24, ran a small tea-and-samosa stall from a rented room in the identical colony and one other counter close to the Mahatma Gandhi Bus Station in Imlibun, south Hyderabad. The stall, investigators say, was a canopy — a technique to appear as if an atypical vendor whereas secretly supplying SIM playing cards in bulk to maintain the operation working.
By the time police swooped in, that they had uncovered over 500 SIM playing cards, with 80 plugged into the gadget and one other 100 saved in reserve for future use. The prison operation continued for seven months — from February to September 2025 — till it was lastly dropped at an finish with the total scale nonetheless being assessed.
A burgeoning rip-off
What occurred in his kitchen was no anomaly; it was a small node in an unlimited and quickly rising net of digital deception. SIM bins, or compact gadgets able to masking worldwide calls as native ones, have quietly develop into the weapon of selection for cybercrime syndicates behind the booming ‘digital arrest’ rip-off.
In lower than two months, Telangana Police, working with the Department of Telecommunications (DoT), dismantled two such networks. The numbers reveal the size of the menace. So far in 2025, 898 folks throughout Telangana have fallen prey to those scams, collectively shedding ₹55.7 crore, based on knowledge from the Telangana Cyber Security Bureau (TGCSB). During the identical interval, the State has reported 62,345 monetary fraud instances, with losses hovering previous ₹1,042.56 crore.
Some 300 kilometres away, in Jannaram of Mancherial district, Telangana, investigators stumbled upon a near-identical set-up — this time inside a cramped, rented room with peeling blue partitions and a naked stone ground.
On a skinny mat lay 5 SIM bins, their tiny lights blinking in mechanical rhythm. A modem and inverter saved the system alive throughout energy cuts, whereas a whirring air-conditioner prevented the gadgets from overheating as they pushed by lots of of calls each day.
At first look, it appeared like nothing greater than an improvised workspace. The males behind it — an unemployed diploma holder, a farmer, a labourer and his youthful brother — appeared as atypical as their environment. But in simply two months, that they had routed calls that triggered 14 digital arrest scams throughout India — 11 in Telangana and one every in Delhi, Uttar Pradesh and Tamil Nadu — siphoning off not less than ₹1.6 crore.
Their operation was eerily disciplined. Working between 10 a.m. and 5 p.m., they mirrored authorities workplace hours, giving their deception a veneer of legitimacy. Each name they routed impersonated a legislation enforcement officer, scaring victims into transferring their life financial savings.
When investigators combed by the house, they discovered the operation’s actual spine — 230 SIM playing cards from Jio, Airtel and Vodafone Idea networks, illegally sourced from a number of places, together with Parvathipuram in Andhra Pradesh.
The selection of location was no coincidence. Jannaram’s weak cell community, with only a handful of 4G towers and no 5G protection, made exact location monitoring extraordinarily difficult.
“The space has just one tower, which hosts a number of telecom networks however no 5G connectivity,” says Inspector Krishna Murthy of Ramagundam Cyber Crime Police Station. “If there was a 5G tower, we may have obtained a Type A location, giving actual coordinates. But with solely a 4G tower, we may get simply an E-type location: we knew the overall space, however not the exact spot. It took us days of subject inquiry, CDR [call detail record] evaluation of an energetic name earlier than we may lastly pinpoint one of many accused.”
Human price of the rip-off
Among the numerous victims was a 76-year-old retired authorities physician from Madhura Nagar. On September 5, she answered a name from some males claiming to be officers of Bengaluru police. Over the following 70 hours, she was repeatedly accused of offences starting from human trafficking to money-laundering, proven fabricated paperwork purporting to be from the Supreme Court, Reserve Bank of India and Enforcement Directorate, and coerced into transferring ₹6.6 lakh to a checking account managed by the fraudsters. Alone at residence, and terrified, she complied.
Police mentioned her daughter-in-law was away and returned solely after the physician started complaining of uneasiness. On September 8, she developed extreme chest ache and was rushed to a non-public hospital in Hyderabad, the place she died of cardiac arrest. Her sons, who dwell in West Bengal and Bengaluru, realized the total horror of the rip-off solely after the funeral on September 9.
According to Assistant Commissioner of Police R. G. Siva Maruthi, the fraudsters continued to ship messages to her cellphone even after her dying, underlining the chilly, mechanical relentlessness of the racket.
Widening the probe, police arrested two males in Maharashtra: Shankar Supur, 38, a water-purifier technician from Kolhapur district whose checking account was used to launder the proceeds, and Vishwas Dattatraya, 35, a businessman from Sangli district, recognized as an account provider.
Cybercrime groups from Hyderabad had been additionally dispatched to north Karnataka to trace different suspects. Maruthi says investigation is beneath technique to establish the masterminds and seize the gadgets used within the rip-off.
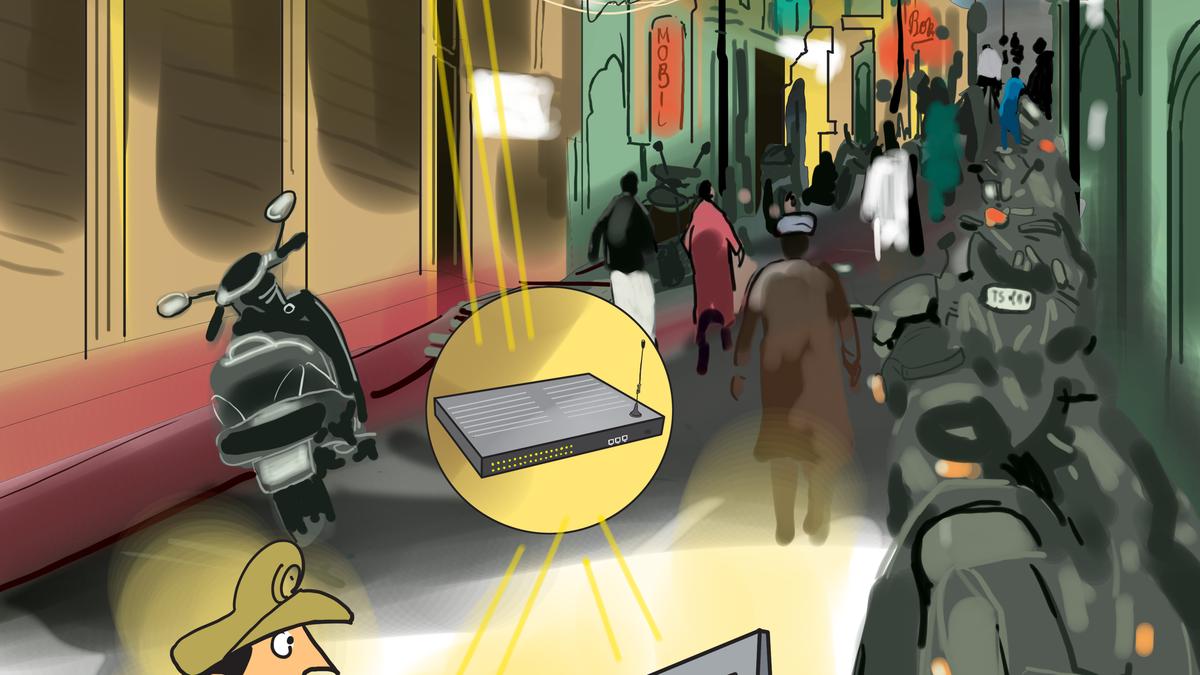
Inside a SIM field
Those gadgets, unremarkable black or gray bins, conceal the fraud’s technical engine: a tangle of SIM slots that may maintain 32 to 512 SIM playing cards, every registered beneath completely different identities or IMEIs (International Mobile Equipment Identity).
A SIM field seized throughout a police raid at a house in Hafiz Baba Nagar colony in Hyderabad final month. | Photo Credit: ARRANGEMENT
Instead of utilizing licensed worldwide telecom gateways, the perpetrators divert calls over the web by way of Voice over Internet Protocol (VoIP). The SIM field converts the VoIP name into an area name and pushes it onto the cell community by one in all its many SIMs. To victims, the incoming quantity appears home, masking the worldwide origin.
The economics of the rip-off make it environment friendly and fleeting. Many SIMs are low cost or obtained with cast paperwork, permitting criminals to pay solely native tariffs whereas worldwide callers are billed at supply. For investigators, the mixture of spoofed numbers, abroad servers and speedy SIM-swapping, generally inside 24 hours, turns each lead right into a vanishing path, complicating efforts to map the community and produce its architects to justice.
Tracking the invisible
The hunt for the machines begins at a desk — on the Department of Telecommunications’ Chakshu portal, the place digital footprints mild up like a path of breadcrumbs. Unlike common handsets, the IMEIs of SIM-box slots stand out as uncommon. Investigators lean on patterns too: spikes in name quantity, clusters of quick calls made in fast succession and a number of numbers that keep energetic from the identical location for unnaturally lengthy stretches.
SIM bins are unlawful in India, however their use has surged once more after the federal government banned caller-ID spoofing apps and web sites beneath the Telecommunication Act, 2023. “Since apps that allowed name spoofing are now not operational in India, fraudsters have returned to SIM bins,” says Okay.V.M. Prasad, Deputy Superintendent of Police (cyber crimes), TGCSB. He provides that the gadgets usually are not manufactured in India: “They are shipped from Cambodia and put in domestically beneath the steering of overseas operators.”
To keep away from suspicion throughout cargo, the bins are disguised as on a regular basis electronics. Small knobs over the SIM slots make them seem like quantity regulators, says Prasad, including that these are despatched by common courier providers and delivered anonymously. Installation is low-touch and high-efficiency, guided over video calls that present step-by-step slot SIMs, join energy and hyperlink the field to broadband. Even these with little technical experience can function them with a cellphone and a set of directions.
But a SIM field is nothing with out SIM playing cards. In the Hafiz Baba Nagar case, the provision chain ran by migrant building employees from Odisha, Bihar, Jharkhand and different northern States. POS brokers lured them with presents of free playing cards, then quietly registered two or extra SIMs beneath a single id. The extras had been siphoned off to gas unlawful operations.
That tactic added layers of complexity for investigators. “The subscriber particulars tied to the SIMs belonged to folks from far-off States, whereas the playing cards themselves powered prison networks in completely completely different places,” Prasad factors out. “Not solely does this make monitoring the operation extraordinarily difficult, it additionally places the employees prone to being implicated in scams that they had no half in.”
In Jannaram, the size was industrial: fraudsters amassed 200-300 SIM playing cards linked to a single Aadhaar quantity, paying lakhs to bypass checks. Each card lived briefly: activated as soon as and used simply lengthy sufficient to route calls earlier than being discarded.
Day after day, lots of of those disposable SIMs saved the operation churning. When spent, they had been shredded, flushed down drains or dumped in lakes and gutters, erasing the path nearly as quickly because it was created.
Fault traces in telecom, banking
Investigating SIM field scams in India is fraught with challenges, riddled with loopholes throughout telecom and banking sectors. “We don’t know who’s shopping for these SIMs or who’s utilizing them. Multiple SIM playing cards are being issued on the identical id,” says Murthy.
In many components of town, SIM playing cards are nonetheless brazenly bought at roadside stalls whereas POS brokers, sub-agents and suppliers type an unlimited and unregulated community that’s almost inconceivable to watch. Weak KYC checks on the level of SIM activation, coupled with the covert nature of worldwide name routing, make detection even harder.
“Most SIMs we discover in these instances belong to BSNL and Vodafone,” says Prasad. “These operators usually are not retaining correct checks, and since their networks are nearly extinct when it comes to common use, fraudsters exploit the hole. For them, it’s simpler to purchase in bulk and more durable for anybody to note.”
Even when SIMs are seized, tracing their exercise is sluggish and cumbersome. “We should depend on telecom operators for particulars like name logs, timings and volumes. If the operators are sluggish or don’t cooperate, the investigation drags on for weeks,” he explains.
The banking system additionally presents vulnerabilities. Fraudsters typically use mule accounts to shortly transfer stolen funds, that are then transformed into cryptocurrency, successfully disappearing into untraceable channels.
And pinpointing who runs the SIM bins is one other problem. While the DoT’s Chakshu portal helps flag suspicious gadgets and their common places, figuring out actual spots requires old-school fieldwork and intensive floor intelligence. Many bins additionally function by worldwide servers, shielding the masterminds behind a number of digital layers.
As investigators chase disappearing trails by servers, SIMs and mule accounts, one fact is simple: expertise might have made scams borderless, however India’s defences stay fragmented. Until telecom operators, banks and legislation enforcement companies tighten coordination, the following SIM field may already be blinking quietly in yet one more unsuspecting residence.
(Frauds of this nature may be reported to ‘1930’ helpline or at ‘www.cybercrime.gov.in’. In emergencies, one can attain out by way of WhatsApp on 8172665171)



Leave a Comment